Installation and Setup
Enabling LiveAssurance (BCIA)
◦ SSH into the LiveNX server CLI.
◦ Enter root mode: sudo su.
◦ Navigate to the LiveAssurance working directory: cd /data/bcia.
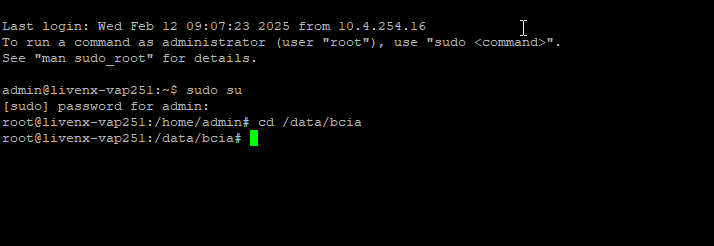
◦ Verify the LiveAssurance files: ls -la.
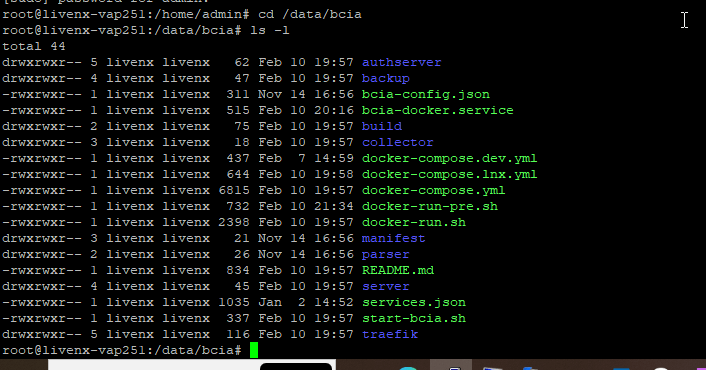
◦ Initiate Docker: sudo ./docker-run-pre.sh (run once).
◦ Start LiveAssurance: ./start-bcia.sh
◦ Access LiveAssurance via a browser at :5443 .
Accessing the LiveAssurance Web Interface
◦ Open :5443 in a browser.
◦ Log in using default credentials (admin/admin123!).
◦ Acknowledge the LiveAssurance Insight Confirmation.
Changing Default Credentials
◦ Navigate to Settings > Users.
◦ Click on the admin user and select Edit.
◦ Provide First Name, Last Name, and enable "Ask for password change at next login". It will ask to change the password on next login.
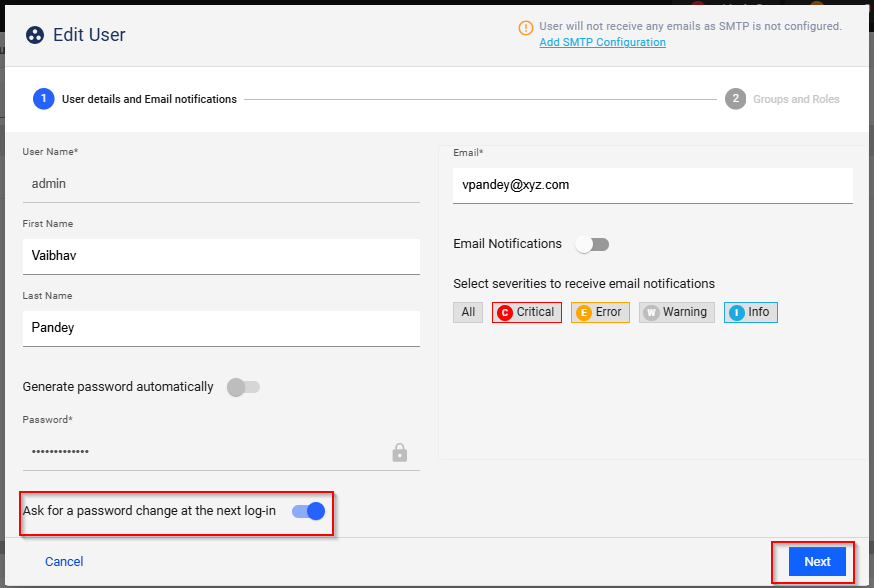
◦ Click Next and then Save.
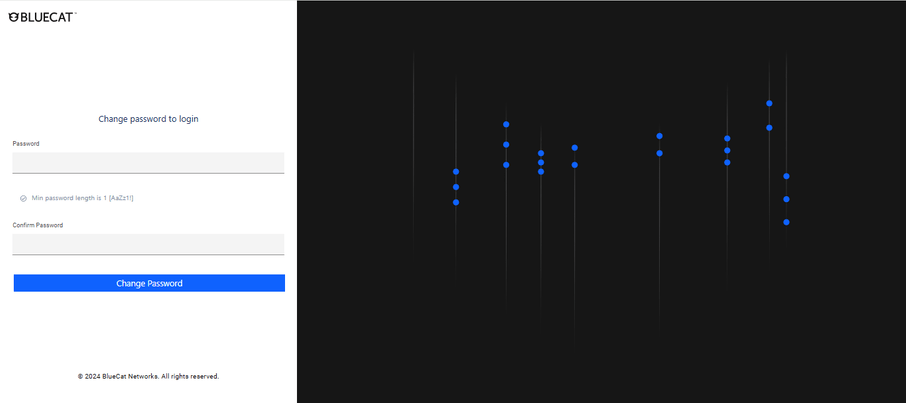
◦ Log out and log back in to change the password.
Device Onboarding and Credential Management
Creating Credential Sets
The first step to inspecting your devices is to create the credential set - the login credentials that will be used to query the devices.
◦ Navigate to Devices > Credential Sets.
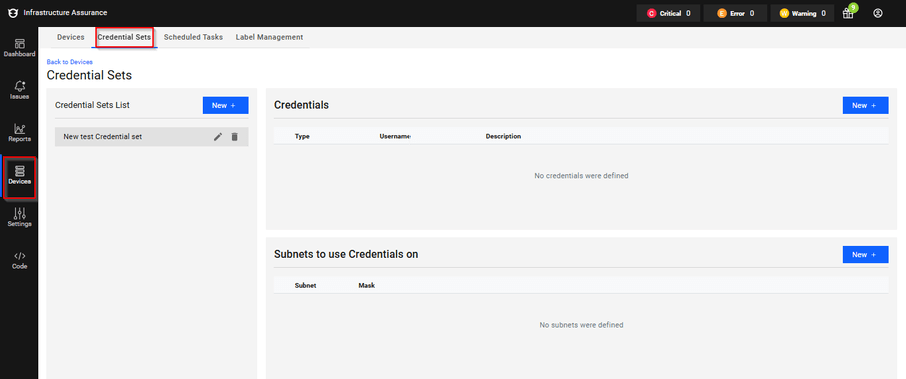
◦ Click New to create a credential set.
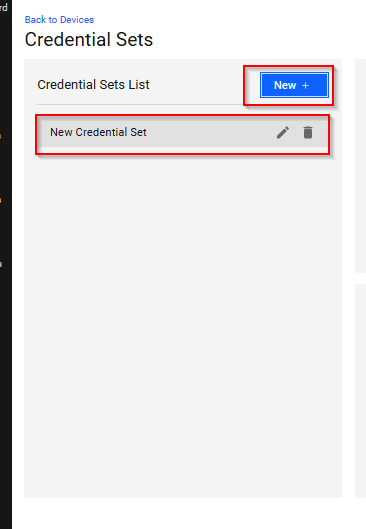
◦ To Create Credentials, click on New to create New Credential Define a custom name and select a credential method:
◦ Username + Password
◦ SH Private Key
◦ SNMPv2
◦ SNMPv3
◦ Configure the username, password, and description.
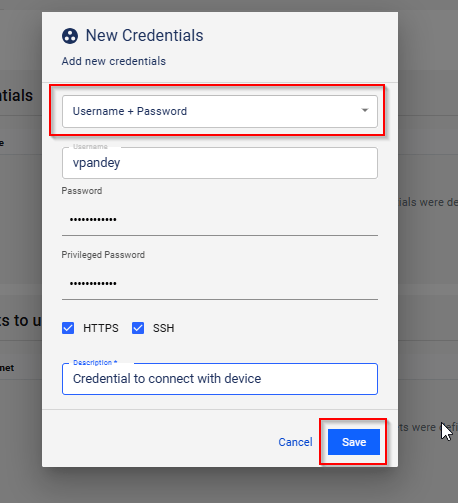
Configuring Subnets for Credentials
The credentials also include the subnet which will use those credentials. If all of your devices are using the same credentials, you can simply set this to 0.0.0.0/0 to have it apply to all devices. Otherwise, if your devices use different credentials, you can create multiple credential sets, and then specify the network and mask for each (which can be an exact IP address such as 94.94.94.17/32 or a subnet such as 94.94.0.0/16).
If there are overlapping Subnets (such as 94.94.94.17/32 and 94.94.0.0/16), the LiveAssurance server will try to connect using the most specific subnet. If those credentials fail, it will then try the next most specific subnet. In our example, the /32 subnet would be tried first and then the /16 subnet.
◦ To add the Subnets, click on the New button to add the subnets.
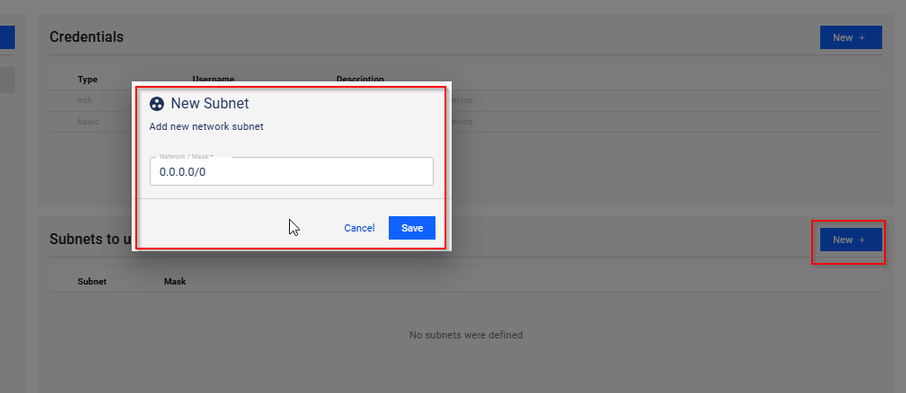
◦ Assign credentials to specific subnets.
◦ Use 0.0.0.0/0 for all devices.
◦ Configure multiple credential sets for different subnet ranges.
◦ If overlapping subnets exist, LiveAssurance prioritizes the most specific subnet.
Adding Devices for Inspection
◦ Navigate to Devices > Device Inventory.
◦ Click New Device +.
◦ Enter the device name and IP address.
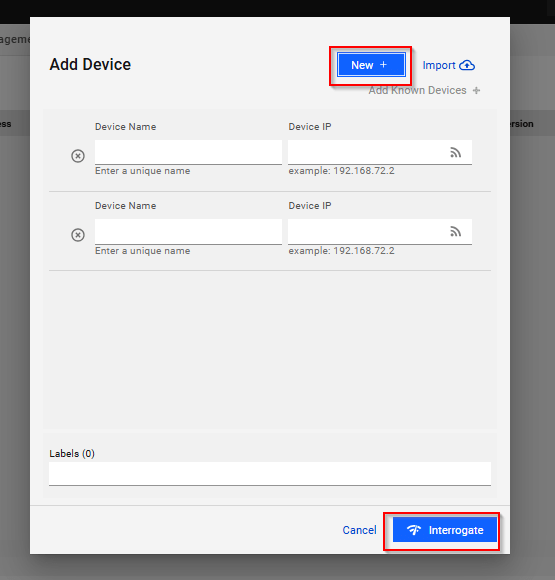
◦ Click Interrogate.
LiveAssurance will interrogate the device (using the credential sets you have created) to determine the device vendor, OS, etc. If the LiveAssurance server is unable to communicate with the device, it will return an error. The most common reasons for a communication issue are:
◦ An issue with the credentials - either
◦ You have mis-typed the username/password in the Credential Set.
◦ The device’s IP Address is not in the subnet(s) assigned to the Credential Set.
◦ Those credentials don’t exist on that device or don’t have the correct permissions.
◦ Connectivity issues between the device and the LiveAssurance server. This could be,
◦ Basic connectivity between LiveAssurance server and device. The easiest way to test this is to logon directly to the LiveAssurance server’s Linux interface and ping the device.
◦ SSH connectivity between the LiveAssurance server and the device. Validate that SSH is enabled on the device using port 22
LiveAssurance queries the firewalls on a scheduled basis, varying from every minute to every day depending on the data being retrieved. You should therefore begin to see Alerts within a few minutes.